In today’s digital landscape, the cost of a data breach can be staggering, with an average price tag of $4.3 million. The demand for robust cybersecurity solutions is increasing as clients and industries require businesses to uphold a certain level of security. This means that investing in cybersecurity is not a typical expense, but a business-savvy, financially wise strategy. In this article, we’ll explore what cybersecurity solutions are, what options exist, how to choose, implement, and optimize the right strategy for your business, and trends for 2023.
What Are Cybersecurity Solutions?
Cybersecurity solutions encompass a wide range of tools, technologies, and services designed to mitigate cyber threats and protect digital assets from unauthorized access, data breaches, and other malicious activities. Cybersecurity solutions play a critical role in maintaining the confidentiality, integrity, and availability of information systems and safeguarding sensitive data, ensuring the smooth operations of your business in all industries and of all sizes. Common examples of such solutions are employee training programs, antivirus software, and firewalls.
Baseline Cybersecurity Solutions
To safeguard against cyber threats, it is not always necessary to invest in complicated and expensive solutions. Phishing and ransomware are significant risks for businesses of all sizes, in both the public and private sectors. Yet, effective remedies for these attacks can be achieved through training, data protection, and access control.
Cybersecurity Training
Data Protection
One effective data protection solution is an encrypted cloud backup program, which regularly automatically copies your data to secure cloud locations. Backup encryption provides an additional layer of protection, rendering the data unreadable and unusable even if hackers gain unauthorized access to your backup. Solution providers in this space include NordLocker, Acronis, Idrive, and CrashPlan.
Access Control
Access control solutions ensure that only authorized users can access your systems. Strong passwords alone are no longer sufficient, as hackers use a range of methods such as phishing attacks, social engineering, automated password guessing, and malware to steal credentials. Access control solutions are particularly important for remote teams, where employees access systems via insecure networks, often on personal devices.
The most easily implementable and important access control solution for your business is multi-factor authentication (MFA), which prevents 30–50% of access-related cyberattacks. MFA requires users to provide multiple forms of identification. A common example of MFA is when users enter a password and a uniquely generated code is sent to their mobile device to log in.
Advanced Cybersecurity Solutions for Enhanced Protection
Network Protection
Prominent network cybersecurity solutions include:
- DDoS protection: DDoS protection solutions are defensive measures that monitor traffic to mitigate and prevent distributed denial-of-service (DDoS) attacks, safeguarding networks and online services by filtering and blocking malicious traffic.
Network cybersecurity solutions are an overarching category, and as such some of the solutions discussed in the remainder of this section also pertain to network security.
Endpoint Protection
In the landscape of remote work and device proliferation, ensuring robust endpoint protection has become paramount to safeguarding sensitive company data. From laptops and mobile phones to wearables, medical devices, scanners, and Internet-of-Things (IoT) devices, endpoints serve as potential gateways for cyber attacks, making effective security solutions indispensable.
Statistics from IBM reveal that a staggering 70% of data breaches stem from vulnerabilities in endpoint devices. With personal devices regularly utilized for work purposes and work devices occasionally used for personal activities, the risk landscape has expanded exponentially.
To combat these threats, organizations must deploy comprehensive endpoint cybersecurity solutions. Such solutions are designed to be installed directly on individual devices, systematically analyzing their files, processes, and systems to identify any signs of suspicious or malicious activity. Examples of widely used endpoint protection solutions include Crowdstrike, Sophos, Kaspersky, and SentinelOne.
Enterprise Endpoint Protection Solutions
Audit Log Management
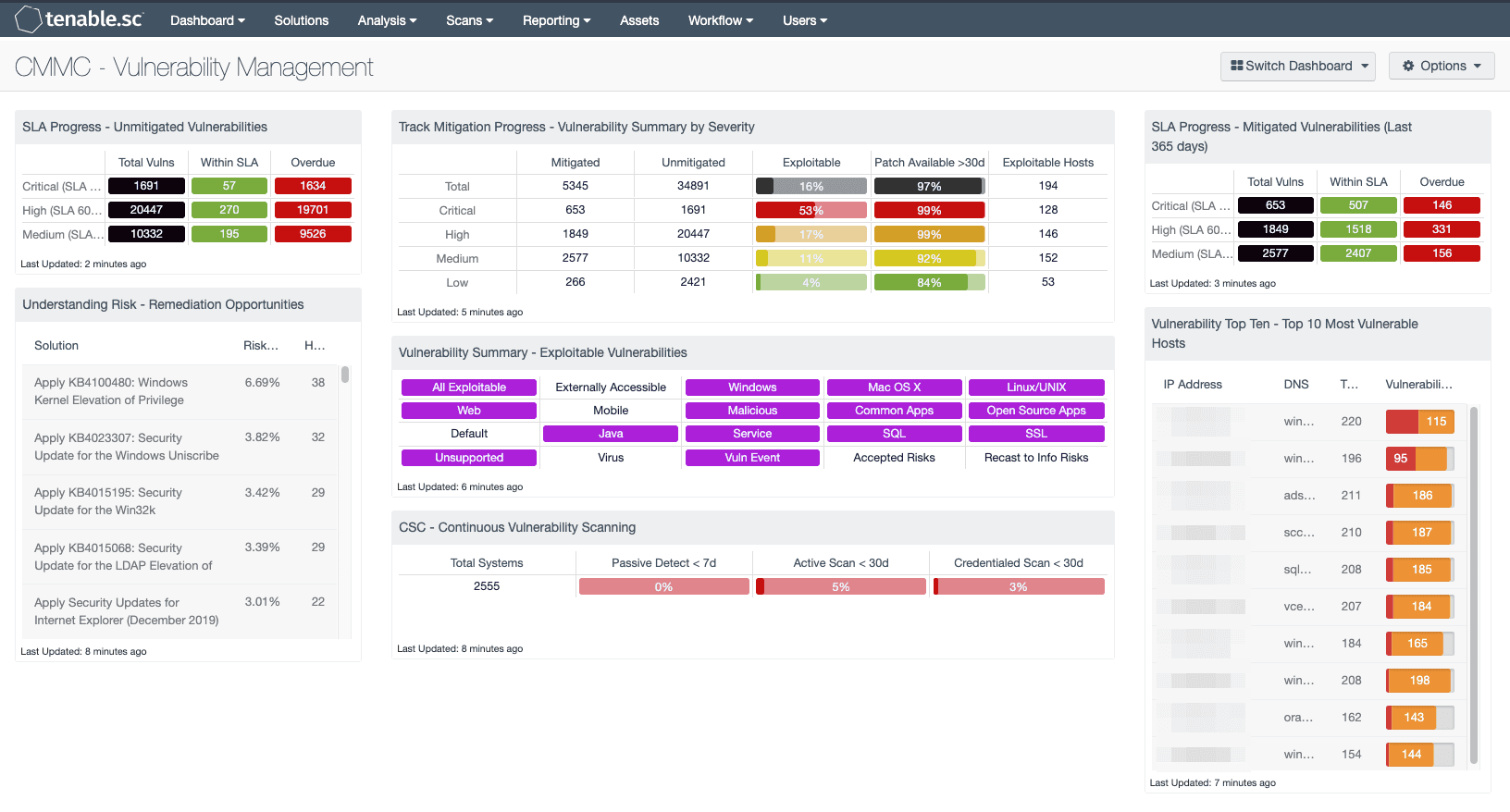
Vulnerability Management
Enterprise Vulnerability Management Solutions
Penetration Testing
Penetration testing services are offered by independent security professionals, specialized penetration testing companies, and managed security service providers (MSSPs). Prominent solution providers in the field of penetration testing include Bugcrowd, HackerOne, ImmuniWeb, and Gcore.
Specialized Solutions
When it comes to protecting specific technologies, specialized solutions are essential. There are three main types of specialized solutions, aimed respectively at applications, cloud, and IoT. Let’s look at each in turn.
Application Security
Application security solutions play a critical role in safeguarding the software that drives business operations. From design to production, these solutions provide an additional layer of protection, mitigating the impact of potential attacks.
There are various types of application security solutions available, each addressing specific aspects of application protection:
- Web application firewalls (WAFs): WAFs act as gatekeepers, protecting all your web resources, including web applications and APIs, against unauthorized access to confidential data. By monitoring traffic in real time, WAFs can enforce preset rules to block malicious requests and thwart potential attacks. Gcore WAF is an example of such a solution. Our tool utilizes machine learning to monitor application traffic and promptly block access if malware is detected.
- Static application security testing (SAST): SAST focuses on reviewing an application’s code to identify common coding errors, insecure coding practices, and known security weaknesses. By analyzing the codebase, SAST tools help developers proactively address vulnerabilities during the development lifecycle.
- Dynamic application security testing (DAST): DAST takes a different approach by monitoring a running application and performing real-time penetration testing. By sending various unusual or malicious inputs to the application, DAST tools evaluate how it responds and detects potential vulnerabilities or bugs. Developers receive detailed reports highlighting identified vulnerabilities.
Veracode and Checkmarx offer both SAST and DAST functionality.

- Runtime application self-protection (RASP): RASP solutions take application security a step further, residing inside the application environment itself. Embedded in the runtime environment, RASP can accurately distinguish between malicious and legitimate actions. Fortify is one well-known example of RASP.
Cloud Security
Cloud security solutions safeguard assets hosted in cloud environments. These solutions encompass both on-premises network security measures, such as firewalls, VPNs, and intrusion detection systems, as well as cloud-specific solutions.
Cloud workload protection platforms (CWPPs) monitor the usage of cloud resources by specific applications and detect any suspicious activities. Acting as intermediaries, cloud access security brokers (CASBs) provide an additional security layer between cloud users and providers. Cloud security posture management solutions (CSPM) focus on identifying and resolving cloud misconfigurations.
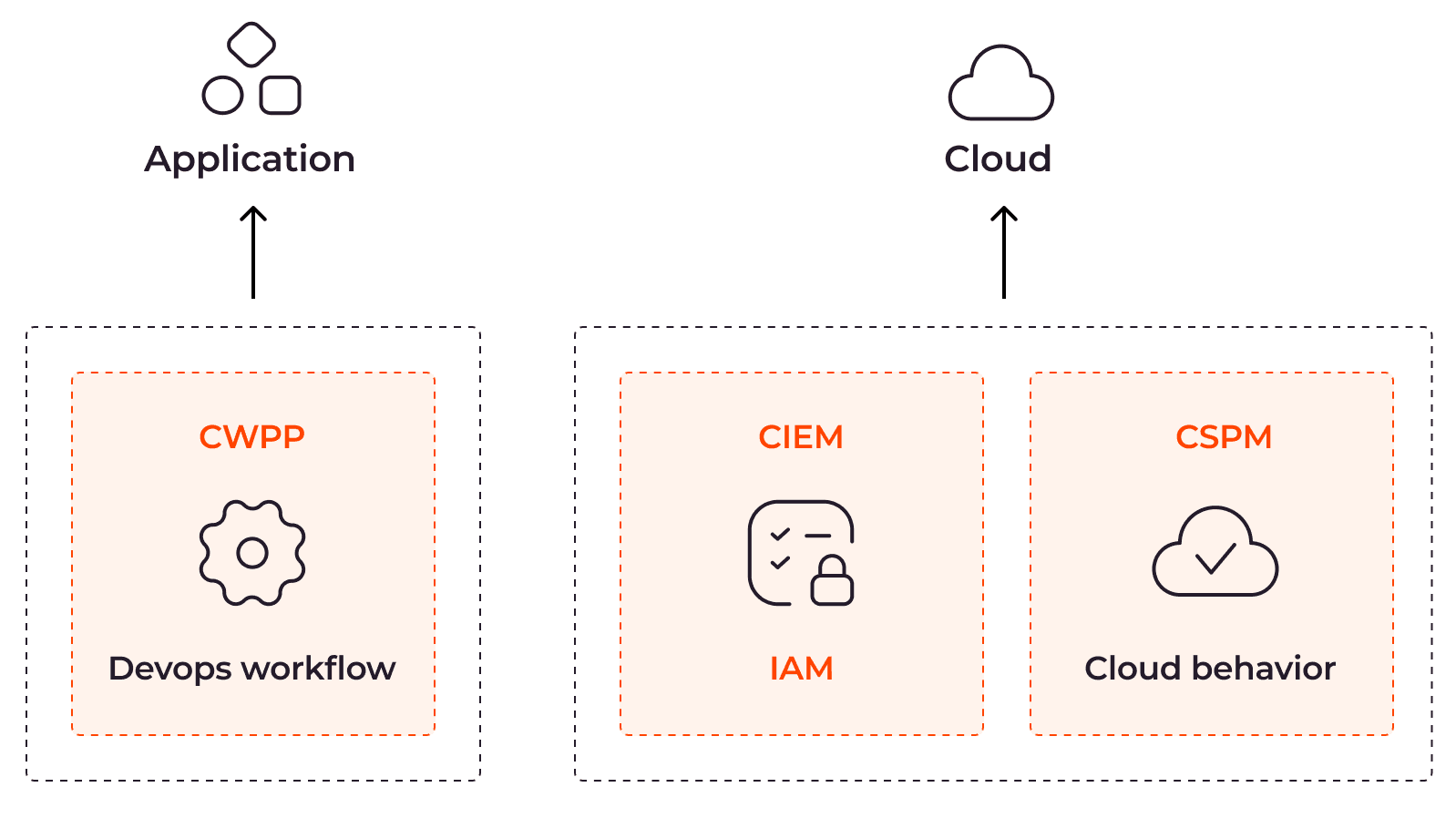
While many cloud providers offer built-in security solutions or as extensions, some organizations require specific cybersecurity controls. Third-party cloud security solutions like Sophos Central, Check Point CloudGuard, and Proofpoint deliver comprehensive protection and ensure the integrity of cloud assets.
IoT Security
IoT security solutions safeguard the wide range of devices that connect to the internet and interact with one another. This includes a wide range of technologies, such as contactless payment systems, medical smart wearables, and smart sensors.
As the IoT landscape expands, so does the potential risk. According to a 2022 report by IBM, the average cost of a data breach increases by $152,465 in an IoT environment, highlighting the urgent need for robust security measures.
How To Optimize Your Cybersecurity Solutions: A Practical Guide
#1 Create an Asset Inventory
#2 Review Legal and Industry Requirements
#3 Conduct a Risk Assessment
Identify vulnerabilities and assess their potential impact and likelihood of occurrence. Prioritize them based on their significance to and potential impact on your organization’s security. Deloitte’s research reports that 56% of high performing companies conduct qualitative risk assessments to optimize ROI. Use relevant questions from the below list informed by governmental best practices to guide your risk assessment process.
- Which assets are connected to your network?
- What levels of protection do the assets need?
- Who can access the assets?
- Where are the assets stored?
- How are the assets currently protected?
- What threats do the assets face?
- What internal processes (incident response plan) are in place when an incident occurs?
#4 Align with Business Goals
#5 Regularly Update Cybersecurity Infrastructure
Recognize that your company’s processes are dynamic, and that changes in operations may require adjustments to your cybersecurity measures. Conduct annual reviews of your cybersecurity infrastructure, as 66% of companies with high cyber performance do.
Implementing Cybersecurity Solutions to Meet Compliance Requirements
To ensure compliance and protect your business:
- Understand applicable standards: Research and explore the cybersecurity standards followed by companies in your industry or niche. This will give you insights into the best practices and requirements relevant to your business.
- Evaluate data: Assess the type and extent of data you handle. Understanding the sensitivity and criticality of the data will help you determine the level of security measures required to protect it adequately.
- Weigh compliance benefits: Compare the benefits of compliance with potential consequences of non-compliance. While some requirements may be recommended but not obligatory, it is essential to consider the potential risks and liabilities associated with non-compliance.
Here are some examples of common regulations that require specific cybersecurity solutions:
- Health Insurance Portability and Accountability Act (HIPAA): If you handle personal health information, compliance with HIPAA is mandatory. This regulation necessitates the implementation of access control, audit logging, and data protection solutions to safeguard sensitive healthcare data.
Outsourcing Cybersecurity
According to IBM, organizations that opt for managed security services can reduce the average cost of data breaches by $69,100, emphasizing the value of outsourcing. There are several common options for outsourcing cybersecurity:
- Specialized managed security solutions: These services provide you with a tool and help you to manage it. For example, Gcore offers managed network and application cybersecurity solutions.
By outsourcing cybersecurity to external providers, businesses can tap into a wealth of knowledge and experience, ensuring robust protection against evolving threats while reducing the burden on in-house employees. The expertise, resources, and advanced technologies offered by these providers enable organizations to strengthen their security posture, while also benefiting from cost savings and round-the-clock vigilance.
Top Cybersecurity Solutions Trends In 2023
The evolving cybersecurity landscape is driving significant changes and innovations in cybersecurity solutions, particularly impacting enterprises and industries with high cybersecurity dependencies, like finance, healthcare, and retail. However, it is crucial for all organizations in all sectors and of all sizes to stay informed about these trends in order to optimize their cybersecurity efforts and return on their cybersecurity investment. Let’s explore three of the top cybersecurity trends for 2023: AI, zero trust, and quantum-safe cryptography.
Artificial Intelligence
The widespread adoption of AI extends to cybersecurity. Cybersecurity providers are actively integrating machine learning capabilities into their solutions. In fact, by 2025, around 82% of IT and security decision-makers plan to invest in AI-driven cybersecurity solutions.
Zero Trust Framework
Gartner forecasts that by 2026, 10% of large companies will have mature zero-trust programs in place, a significant increase from less than 1% in 2023. Recognized organizations have already established standards, such as NIST 800-207, which can guide companies in implementing a zero-trust infrastructure.
Quantum-Safe Cryptography
Although quantum computers are not available today, the pace of technological progress is rapid. For instance, in May 2023 IBM opened access to its latest Osprey Quantum Processor, boasting an impressive 413 Qubits. Such advancements indicate that the era of practical quantum computing is drawing closer.
Recognizing the need for quantum-resistant encryption, the US Department of Commerce’s National Institute of Standards and Technology (NIST) has taken a proactive role. NIST announced the development of a post-quantum cryptographic standard, which is expected to be finalized by 2024. This standard will provide guidelines for implementing cryptographic algorithms that can withstand attacks from powerful quantum computers.
Conclusion
To assist you in navigating the complex landscape of cybersecurity solutions, we invite you to explore Gcore’s security tools—like DDoS Protection—or consult our experts. Our resources provide valuable insights and guidance on selecting the most suitable cybersecurity solutions for your organization.
Under attack? Get help now.
Related articles
Subscribe to our newsletter
Get the latest industry trends, exclusive insights, and Gcore updates delivered straight to your inbox.